Unified Notification Architecture for Multi-Channel Systems

How large organizations eliminate notification fragmentation—without slowing down product teams
By François Bossière, Ph.D. in AI and Computer Science, Founder of Polynom (AI consulting firm & AI products editor)
TL;DR
When an organization operates multiple products—customer-facing apps, internal tools, partner portals—it almost always ends up fragmenting notifications. Each team integrates its own email, SMS or push provider, writes its own templates, and applies its own rules. Over time, this creates a hidden but very real cost.
Customers experience inconsistent tone, branding and cadence. Compliance teams struggle to reconstruct who was notified, when, and through which channel. Engineering teams repeatedly rebuild the same plumbing: retries, idempotency, templates, analytics. Velocity slows down precisely where it should be highest.
This article introduces the concept of a unified notification hub: a platform capability that centralizes policies, templates, preferences and delivery tracking, while allowing product teams to remain focused on business features.
The narrative uses a banking platform as a concrete example, but the architecture applies just as well to marketplaces, SaaS products, logistics platforms, insurers or public-sector systems.
Who this is for
This article is written for technical leaders and senior engineers who are already operating at some scale. It is intended for CTOs and CPOs overseeing a growing portfolio of applications, for staff and lead engineers building internal platform services, and for architects responsible for compliance, observability and operational reliability.
If your organization has already integrated two or three notification providers independently—SES here, SendGrid there, Twilio somewhere else—you are almost certainly facing a platform problem rather than a local one.
1. The Problem: Fragmented Notifications at Scale
In a typical bank:
- Digital banking sends transaction alerts
- Trading systems emit execution confirmations
- Credit systems handle loan reminders
- Fraud engines push security alerts
Each system often integrates directly with a provider (SMTP, Twilio, push gateways).
The hidden tax
The cost of fragmented notifications is rarely visible on a single roadmap, but it accumulates steadily. Branding, tone and timing vary from one system to another, which erodes customer trust. Opt-outs and quiet hours are implemented inconsistently, or not at all, leading to user frustration and regulatory exposure. From a compliance perspective, there is no single audit trail that can reliably answer the question: who was notified, about what, and when?
On the engineering side, each team reimplements the same concerns—retry logic, idempotency, templating, provider-specific quirks—often with slightly different semantics. As the number of applications grows, this duplication increases faster than linearly.
A very practical signal of this situation appears when a simple copy change requested by marketing or compliance requires multiple code changes and deployments across several teams. At that point, the issue is no longer content—it is architecture.
2. The Core Idea: A Unified Notification Hub
A unified notification system is a platform service that all applications depend on for customer communications.
Applications express intent:
“Notify this customer about this event, with this context.”
The notification hub decides how, when, and whether to deliver.
What gets centralized (and why it matters)
The purpose of a unified notification hub is not to slow teams down, but to remove an entire class of recurring problems from their backlog. Channel abstraction ensures that applications never deal with the mechanics of HTML emails, SMS length limits or push payloads. Template management becomes a shared capability, with proper versioning, localization and experimentation.
Preference enforcement is applied consistently across all products, whether it concerns opt-outs, quiet hours or frequency caps. Delivery tracking and provider reconciliation are handled once, in one place, instead of being partially reimplemented everywhere. Finally, observability and analytics become reliable because all notifications flow through a single system.
The net effect is that product teams stop rebuilding infrastructure and can focus on shipping business value.
3. Macro Architecture: System Positioning
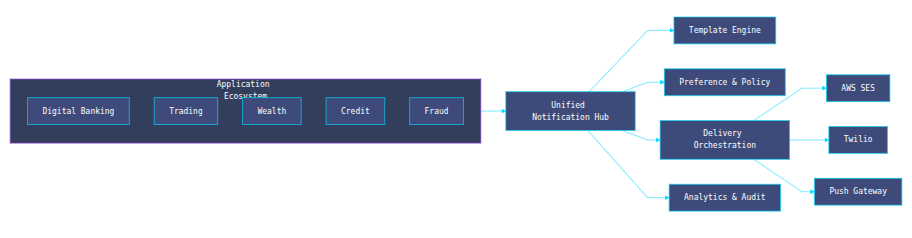
Architectural principles (the ones that actually move the needle)
A few architectural principles make the difference between a notification system that merely centralizes APIs and one that actually scales.
First, notification delivery must be event-driven by default. Sending a notification should never block a business workflow. Applications publish intents asynchronously, and queues absorb traffic spikes while isolating failures.
Second, multi-tenancy must be treated as a first-class concern. Every request is scoped by application or tenant, which allows proper isolation for rate limits and failures, per-tenant analytics, and clear governance over templates and policies.
Third, channel abstraction is essential. Applications should never format HTML or think about SMS character limits. They select a notification type, and the platform renders appropriate content for each channel.
Finally, policy enforcement belongs at the platform level. Preferences, legal constraints, quiet hours and overrides should be enforced centrally, not reimplemented by each team in slightly different ways.
4. Conceptual Model: The Notification Lifecycle
A unified notification system works because it standardizes the lifecycle of every notification, regardless of its origin or channel. Each notification starts as an intent, expressed via an API call or an event. That intent is validated and deduplicated through idempotency rules. The system then resolves the appropriate template based on notification type, channel and language, and evaluates user preferences such as opt-outs, quiet hours and rate limits.
Once policies are satisfied, the system orchestrates delivery across one or more channels. Each delivery attempt is tracked independently, and external provider feedback is reconciled asynchronously. Finally, all of this information feeds metrics, dashboards and audit logs.
This lifecycle remains remarkably stable across industries. What changes from one domain to another are the notification types and the policies applied—not the underlying flow.
5. Core Domain Concepts (Minimal Models)
Delivery vs Attempt
This distinction keeps the model honest:
- Delivery = business intent (“notify customer X about event Y”)
- Attempt = technical execution (“send via email/SMS/push”)
It enables partial success (SMS succeeds, email bounces) and clean retry semantics.
class MessageDispatch:
dispatch_uuid: UUID
source_system: str
message_blueprint: str
deduplication_token: str
transports: list[str]
payload_data: dictclass TransportExecution:
dispatch_reference: UUID
transport: str
execution_outcome: str # QUEUED | DISPATCHED | REJECTED
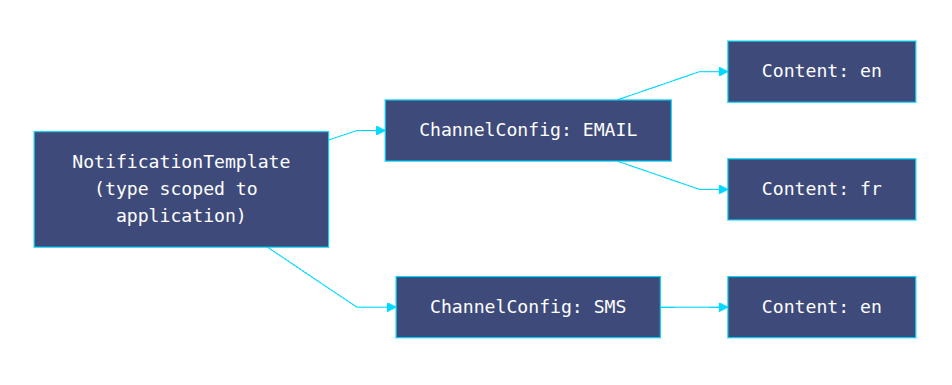
provider_tracking_ref: str | NoneTemplate hierarchy (critical insight)
Templates vary along three independent axes:
- Notification type (business event)
- Channel (email, SMS, push, in-app)
- Language
Keeping those axes separate avoids a combinatorial explosion and unlocks delegation:
- Product teams manage notification types
- Growth/Marketing updates content safely
- Localization manages translations independently
6. Delivery Orchestration (Structural View)
The orchestration service coordinates—not implements—everything.
class DispatchCoordinator:
async def transmit(request):
dispatch = initialize_dispatch(request)
blueprint = fetch_blueprint(request)
transports = determine_transports(blueprint, request)
transports = apply_consent_rules(transports, request)
for transport in transports:
route_through_transport(dispatch, transport)Design intent: orchestration composes specialized services (templates, preferences, channels) rather than embedding provider-specific logic.
7. Channel Abstraction
All providers conform to one contract:
class TransportAdapter(Protocol):
async def dispatch(target_party, rendered_payload) -> TransportResponseBenefits:
- Provider substitution (SES → SendGrid) without refactoring producers
- Circuit breakers and retries per channel
- Fallback strategies for critical alerts (email → SMS)
The provider choice is infrastructure, not business logic.
8. Integration Patterns (Pragmatic Guidance)
Pattern A: Synchronous API
Use for user-triggered, latency-sensitive flows (OTP, confirmations).
response = await dispatch_coordinator.transmit(
source_system="authentication_service",
message_blueprint="one_time_password",
target_party_id="USER-98765",
transports=["TEXT_MESSAGE"],
payload_data={
"verification_code": "123456",
"expiry_minutes": 5
}
)Pattern B: Asynchronous events (default)
Applications emit events; workers deliver independently.
{
"source_system": "securities_platform",
"message_blueprint": "transaction_confirmed",
"target_party_id": "USER-98765",
"transports": ["ELECTRONIC_MAIL", "MOBILE_NOTIFICATION"],
"payload_data": {
"instrument": "AAPL",
"quantity": 100,
"execution_price": 187.42,
"currency": "USD"
}
}Pattern C: Scheduled notifications
Monthly statements, reminders, campaigns. Scheduling lives outside product code but uses the same notification core.
scheduler.schedule_dispatch(
trigger_time="2025-01-01T09:00:00Z",
source_system="billing_platform",
message_blueprint="monthly_statement",
target_party_id="USER-98765",
transports=["ELECTRONIC_MAIL"],
payload_data={
"statement_period": "2024-12",
"total_charges": 1250.00,
"document_url": "https://cdn.example.com/statements/2024-12.pdf"
}
)9. Content Blueprint Structure
Templates vary along three independent axes:
- Message blueprint (business event)
- Transport (electronic mail, text message, mobile notification, internal banner)
- Language
Keeping those axes separate avoids a combinatorial explosion and unlocks delegation:
- Product teams manage message blueprints
- Growth/Marketing updates content safely
- Localization manages translations independently
class ContentBlueprint:
blueprint_name: str
transport_type: str # ELECTRONIC_MAIL | TEXT_MESSAGE | MOBILE_NOTIFICATION
language_code: str
subject_template: str | None
body_template: str
template_variables: list[str]10. Operational Excellence by Design
Operational concerns are not an afterthought in a notification platform; they are part of the design. Observability is mandatory if the system is to be trusted. At a minimum, teams need visibility into delivery success rates per channel, latency distributions, bounce and complaint rates, preference suppressions, and queue backlogs.
Resilience follows naturally from this visibility. Transient provider failures should be handled with retries and backoff. Systemic failures should be contained through circuit breakers. For critical notifications, graceful degradation and channel fallback are often preferable to silent failure.
Security considerations are equally foundational. Personally identifiable information must be encrypted at rest, applications must authenticate strongly when emitting notification intents, and delivery history must be auditable with retention policies aligned to regulation.
11. Why This Architecture Generalizes
Banking is a convenient narrative (high volume + regulation), but the same platform problem appears wherever multiple products communicate with users:
- Marketplaces: buyer/seller lifecycle
- SaaS: billing, incidents, renewal nudges
- Logistics: shipment tracking
- Insurance: claims lifecycle
- Public sector: citizen communications
In all cases, notifications are infrastructure, not a feature.
Conclusion
A unified notification system acts as a force multiplier. It reduces cognitive load for product teams, improves customer trust through consistency, and embeds compliance directly into the architecture rather than layering it on afterward. It also creates a clean foundation for future optimization, including AI-driven routing, timing and content personalization.
When consolidating multiple applications, the priority should be to stabilize the core concepts first: a unified intent model, a clear template hierarchy, consistent preference enforcement, and a delivery model that separates business intent from technical attempts.
How Polynom helps
At Polynom, we design and build production-grade platform capabilities (including unified notifications) for organizations that need to move fast without compromising reliability or compliance.
Typical engagements include:
- Architecture and target operating model for a notification platform
- Migration strategy from legacy, app-local notification stacks
- Implementation acceleration (core services, templates, policy engine, observability)
- AI enhancements (send-time optimization, channel selection, content variants)
If you want a second set of eyes on your architecture, or an implementation plan tailored to your stack and constraints, reach out via Polynom.
About the author
François Bossière, Ph.D. in AI and Computer Science, is the founder of Polynom, a consulting firm specializing in AI product development and software craftsmanship. He helps teams build robust systems where architecture, operations, and product constraints are treated as first-class design inputs.




